Fintech
SEC Proposes Data Security Enhancements to the CAT NMS Plan

Washington, D.C.–(Newsfile Corp. – August 21, 2020) – The Securities and Exchange Commission today proposed amendments to the national market system plan governing the Consolidated Audit Trail (the “CAT NMS Plan”) to bolster the Consolidated Audit Trail’s (“CAT”) data security. While the CAT NMS Plan currently sets forth a number of requirements regarding the security and confidentiality of CAT data, the proposed amendments to the CAT NMS Plan are the latest SEC action to limit the scope of sensitive information required to be collected by CAT and enhance the security of the CAT and the protections afforded to CAT data.
“Data security is an essential pillar of the CAT,” said SEC Chairman Jay Clayton. “The requirements outlined in the proposal, including requiring the removal of sensitive PII, are designed to both (1) significantly reduce the amount of sensitive data collected without affecting the operational effectiveness of the CAT and (2) provide market participants with greater certainty regarding how CAT data will be protected and used. We will continue to evaluate these matters, including to address changes in risks and other matters, as implementation and operation of the CAT continues.”
The public comment period will remain open for 60 days following the date that the release is posted on www.sec.gov.
* * *
Fact Sheet
Action
Today, the Commission voted to propose amendments to the CAT NMS Plan that are designed to enhance the security of the CAT through increased security requirements as well as limiting the scope of sensitive information required to be collected by the CAT.
Comprehensive Information Security Program
The proposed amendments would explicitly define the scope of the CAT’s information security program by adding the term “Comprehensive Information Security Program” (the “CISP”) to set forth all elements of the information security program, inclusive of the proposed Secure Analytical Workspaces.
Security Working Group
The proposed amendments would require the permanent establishment of a security working group that will be composed of the CAT’s Chief Information Security Officer (“CAT CISO”), and the chief information security officer or deputy chief information security officer of each self-regulatory organization that is a participant to the CAT NMS Plan (the “Participants”). The CAT CISO and the Operating Committee may invite other parties to attend specific meetings.
Secure Analytical Workspaces
The proposed amendments would define a Secure Analytical Workspace (“SAW”) as an analytic environment account that is part of the CAT system, and subject to the CISP, where CAT data is accessed and analyzed. The proposed amendments would further require the CISP to establish data access and extraction policies. However, the proposed amendments would explicitly state that each Participant would be allowed to provide and use its own choice of software, hardware configurations, and additional data within its SAW, so long as such activities otherwise comply with the CISP.
The proposed amendments would require Participants to use their SAWs for analyzing CAT data accessed through user-defined direct query and bulk extract tools and for any customer and account data. Participants may only extract from SAWs the minimum amount of CAT Data necessary to achieve a specific surveillance or regulatory purpose. The proposed amendments also set forth a process by which Participants may be granted an exception from using the SAW related to data accessed via user-defined direct query and bulk extract tools.
Online Targeted Query Tool and Logging of Access and Extraction
The proposed amendments would limit the maximum amount of records that regulators can download using an online targeted query tool. The proposed amendments would also enhance logging requirements by requiring logging of extraction of CAT data.
CAT Customer and Account Attributes (Removing Sensitive Personally Identifiable Information)
The proposed amendments would modify the Customer-ID creation process and reporting requirements in accordance with the exemptive order issued by the Commission on March 17, 2020. Specifically, the proposed amendments would no longer require Industry Members to report social security numbers/individual taxpayer identification numbers and account numbers for natural person Customers, and would replace the requirement that the date of birth for a natural person Customer be reported with the requirement that the year of birth for a natural person Customer be reported to, and collected by, the CAT.
Customer Identifying Systems Workflow
The proposed amendments define the workflow for accessing customer and account attributes and establish restrictions governing such access. As described above, Customer Identifying Systems, which contain customer and account attributes, would have to be accessed through a Participant’s SAW. Only Regulatory Staff may access Customer Identifying Systems and such access would have to follow role based access control (“RBAC”) and the “least privileged” practice of limiting access to Customer Identifying Systems and customer and account attributes as much as possible. All queries of Customer Identifying Systems would have to be based on a “need to know” the data in the Customer Identifying Systems, and queries must be designed such that query results would contain only the customer and account attributes that Regulatory Staff reasonably believes will achieve the regulatory purpose of the inquiry or set of inquiries.
Access to Customer Identifying Systems would be limited to two types of access: manual access and programmatic access. For manual access, the proposed amendments generally provide that Regulatory Staff must have identified a Customer(s) of regulatory interest through their own regulatory efforts before they may use manual access to obtain additional information regarding such Customer(s). To use programmatic access, authorization would have to be requested and approved by the Commission pursuant to the process described in the proposed amendments, and Participants approved for such access may programmatically query the Customer Identifying Systems.
Participants’ Data Confidentiality Policies and Regulator Access to CAT Data
The proposed amendments would require the Participants to establish, maintain, enforce and publish identical written data confidentiality policies. Each Participant would establish, maintain and enforce procedures and usage restrictions in accordance with these policies. In addition, the Participants would be required to make the data confidentiality policies publicly available on a website, and on an annual basis each Participant would be required to engage an independent accountant to perform an examination of compliance with the data confidentiality policies.
The proposed amendments would define the term “Regulatory Staff” and the data confidentiality policies adopted by Participants would be required to limit access to CAT data to Regulatory Staff, and certain technology and operations staff, except when there is a specific regulatory need and a Participant’s Chief Regulatory Officer (or similarly designated head(s) of regulation), or his or her designee, documents written approval. The policies would also limit the extraction of CAT data, define the roles and regulatory activities of specific users, and require implementation of the Customer Identifying Systems workflow along with supporting requirements for monitoring and testing.
The proposed amendments would also require that CAT data be accessed only for surveillance and regulatory purposes and forbid the use of CAT data where such use may serve both a surveillance or regulatory purpose, and a commercial purpose (e.g., economic analyses or market structure analyses in support of rule filings).
Secure Connectivity and Data Storage
In addition to requiring connectivity to CAT infrastructure in a manner consistent with current implementation, the proposed amendments would require the Plan Processor to implement “allow” listing, which would limit access to CAT only to those countries where CAT reporting or regulatory use is both necessary and expected. In addition, the proposed amendments would require that data centers housing CAT systems must be physically located in the United States.
Breach Management Policies and Procedures
The proposed amendments would modify existing requirements related to breach management policies and procedures to explicitly require corrective actions and breach notifications to CAT Reporters be a part of the Plan Processor’s cyber incident response plan, modeled after Regulation SCI obligations.
In addition to the security-related items above, the proposed amendments would, consistent with previously granted exemptive relief, explicitly require customer and account attributes to be reported for Firm Designated IDs that are submitted in allocation reports, as is required for Firm Designated IDs associated with the original receipt or origination of an order.
What’s next?
The proposal will be published on SEC.gov and in the Federal Register. There will be a 45-day comment period following publication in the Federal Register.
Fintech
How to identify authenticity in crypto influencer channels

Modern brands stake on influencer marketing, with 76% of users making a purchase after seeing a product on social media.The cryptocurrency industry is no exception to this trend. However, promoting crypto products through influencer marketing can be particularly challenging. Crypto influencers pose a significant risk to a brand’s reputation and ROI due to rampant scams. Approximately 80% of channels provide fake statistics, including followers counts and engagement metrics. Additionally, this niche is characterized by high CPMs, which can increase the risk of financial loss for brands.
In this article Nadia Bubennnikova, Head of agency Famesters, will explore the most important things to look for in crypto channels to find the perfect match for influencer marketing collaborations.
-
Comments
There are several levels related to this point.
LEVEL 1
Analyze approximately 10 of the channel’s latest videos, looking through the comments to ensure they are not purchased from dubious sources. For example, such comments as “Yes sir, great video!”; “Thanks!”; “Love you man!”; “Quality content”, and others most certainly are bot-generated and should be avoided.
Just to compare:
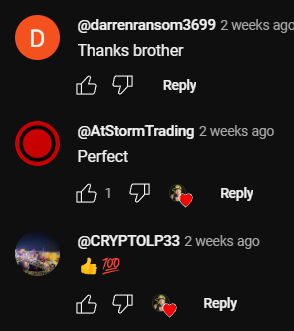
LEVEL 2
Don’t rush to conclude that you’ve discovered the perfect crypto channel just because you’ve come across some logical comments that align with the video’s topic. This may seem controversial, but it’s important to dive deeper. When you encounter a channel with logical comments, ensure that they are unique and not duplicated under the description box. Some creators are smarter than just buying comments from the first link that Google shows you when you search “buy YouTube comments”. They generate topics, provide multiple examples, or upload lists of examples, all produced by AI. You can either manually review the comments or use a script to parse all the YouTube comments into an Excel file. Then, add a formula to highlight any duplicates.
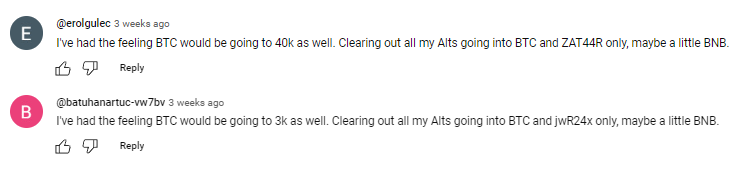
LEVEL 3
It is also a must to check the names of the profiles that leave the comments: most of the bot-generated comments are easy to track: they will all have the usernames made of random symbols and numbers, random first and last name combinations, “Habibi”, etc. No profile pictures on all comments is also a red flag.
LEVEL 4
Another important factor to consider when assessing comment authenticity is the posting date. If all the comments were posted on the same day, it’s likely that the traffic was purchased.
2. Average views number per video
This is indeed one of the key metrics to consider when selecting an influencer for collaboration, regardless of the product type. What specific factors should we focus on?
First & foremost: the views dynamics on the channel. The most desirable type of YouTube channel in terms of views is one that maintains stable viewership across all of its videos. This stability serves as proof of an active and loyal audience genuinely interested in the creator’s content, unlike channels where views vary significantly from one video to another.
Many unauthentic crypto channels not only buy YouTube comments but also invest in increasing video views to create the impression of stability. So, what exactly should we look at in terms of views? Firstly, calculate the average number of views based on the ten latest videos. Then, compare this figure to the views of the most recent videos posted within the past week. If you notice that these new videos have nearly the same number of views as those posted a month or two ago, it’s a clear red flag. Typically, a YouTube channel experiences lower views on new videos, with the number increasing organically each day as the audience engages with the content. If you see a video posted just three days ago already garnering 30k views, matching the total views of older videos, it’s a sign of fraudulent traffic purchased to create the illusion of view stability.
3. Influencer’s channel statistics
The primary statistics of interest are region and demographic split, and sometimes the device types of the viewers.
LEVEL 1
When reviewing the shared statistics, the first step is to request a video screencast instead of a simple screenshot. This is because it takes more time to organically edit a video than a screenshot, making it harder to manipulate the statistics. If the creator refuses, step two (if only screenshots are provided) is to download them and check the file’s properties on your computer. Look for details such as whether it was created with Adobe Photoshop or the color profile, typically Adobe RGB, to determine if the screenshot has been edited.
LEVEL 2
After confirming the authenticity of the stats screenshot, it’s crucial to analyze the data. For instance, if you’re examining a channel conducted in Spanish with all videos filmed in the same language, it would raise concerns to find a significant audience from countries like India or Turkey. This discrepancy, where the audience doesn’t align with regions known for speaking the language, is a red flag.
If we’re considering an English-language crypto channel, it typically suggests an international audience, as English’s global use for quality educational content on niche topics like crypto. However, certain considerations apply. For instance, if an English-speaking channel shows a significant percentage of Polish viewers (15% to 30%) without any mention of the Polish language, it could indicate fake followers and views. However, if the channel’s creator is Polish, occasionally posts videos in Polish alongside English, and receives Polish comments, it’s important not to rush to conclusions.
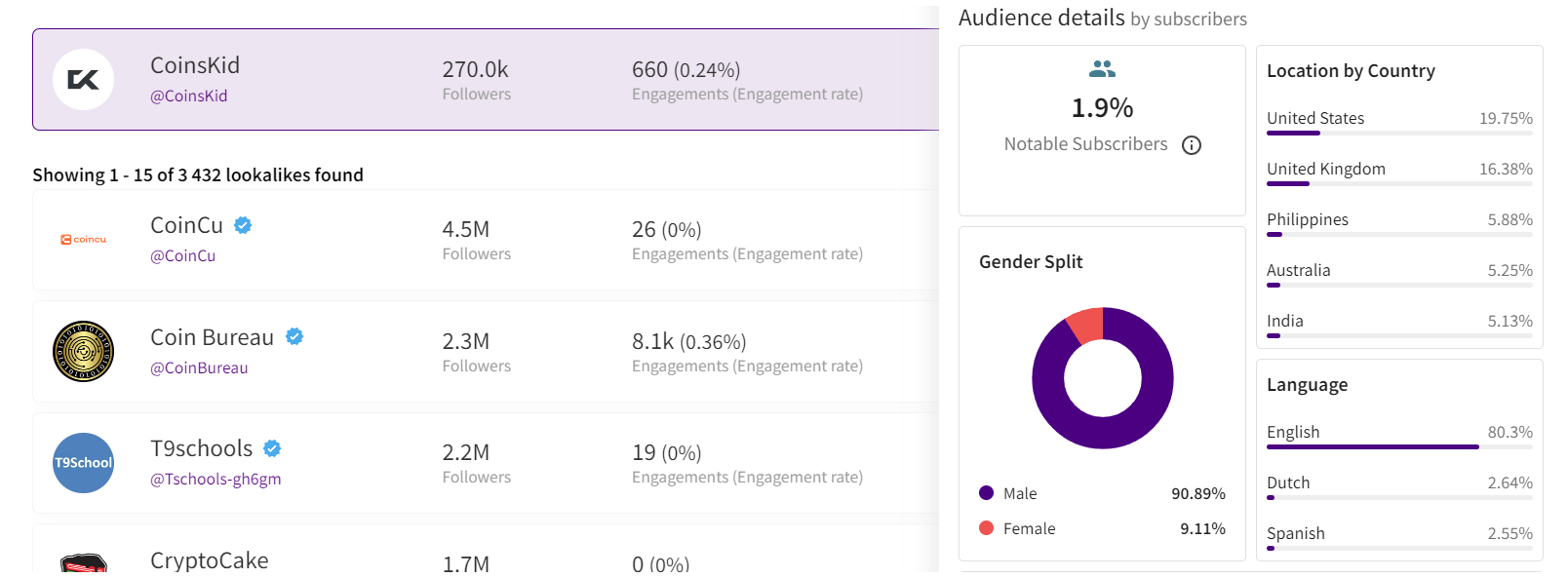 Example of statistics
Example of statistics
Wrapping up
These are the main factors to consider when selecting an influencer to promote your crypto product. Once you’ve launched the campaign, there are also some markers to show which creators did bring the authentic traffic and which used some tools to create the illusion of an active and engaged audience. While this may seem obvious, it’s still worth mentioning. After the video is posted, allow 5-7 days for it to accumulate a basic number of views, then check performance metrics such as views, clicks, click-through rate (CTR), signups, and conversion rate (CR) from clicks to signups.
If you overlooked some red flags when selecting crypto channels for your launch, you might find the following outcomes: channels with high views numbers and high CTRs, demonstrating the real interest of the audience, yet with remarkably low conversion rates. In the worst-case scenario, you might witness thousands of clicks resulting in zero to just a few signups. While this might suggest technical issues in other industries, in crypto campaigns it indicates that the creator engaged in the campaign not only bought fake views and comments but also link clicks. And this happens more often than you may realize.
Summing up, choosing the right crypto creator to promote your product is indeed a tricky job that requires a lot of resources to be put into the search process.

Author
Nadia Bubennikova, Head of agency at Famesters
Fintech
Central banks and the FinTech sector unite to change global payments space

The BIS, along with seven leading central banks and a cohort of private financial firms, has embarked on an ambitious venture known as Project Agorá.
Named after the Greek word for “marketplace,” this initiative stands at the forefront of exploring the potential of tokenisation to significantly enhance the operational efficiency of the monetary system worldwide.
Central to this pioneering project are the Bank of France (on behalf of the Eurosystem), the Bank of Japan, the Bank of Korea, the Bank of Mexico, the Swiss National Bank, the Bank of England, and the Federal Reserve Bank of New York. These institutions have joined forces under the banner of Project Agorá, in partnership with an extensive assembly of private financial entities convened by the Institute of International Finance (IIF).
At the heart of Project Agorá is the pursuit of integrating tokenised commercial bank deposits with tokenised wholesale central bank money within a unified, public-private programmable financial platform. By harnessing the advanced capabilities of smart contracts and programmability, the project aspires to unlock new transactional possibilities that were previously infeasible or impractical, thereby fostering novel opportunities that could benefit businesses and consumers alike.
The collaborative effort seeks to address and surmount a variety of structural inefficiencies that currently plague cross-border payments. These challenges include disparate legal, regulatory, and technical standards; varying operating hours and time zones; and the heightened complexity associated with conducting financial integrity checks (such as anti-money laundering and customer verification procedures), which are often redundantly executed across multiple stages of a single transaction due to the involvement of several intermediaries.
As a beacon of experimental and exploratory projects, the BIS Innovation Hub is committed to delivering public goods to the global central banking community through initiatives like Project Agorá. In line with this mission, the BIS will soon issue a call for expressions of interest from private financial institutions eager to contribute to this ground-breaking project. The IIF will facilitate the involvement of private sector participants, extending an invitation to regulated financial institutions representing each of the seven aforementioned currencies to partake in this transformative endeavour.
Source: fintech.globa
The post Central banks and the FinTech sector unite to change global payments space appeared first on HIPTHER Alerts.
Fintech
TD Bank inks multi-year strategic partnership with Google Cloud

TD Bank has inked a multi-year deal with Google Cloud as it looks to streamline the development and deployment of new products and services.
The deal will see the Canadian banking group integrate the vendor’s cloud services into a wider portion of its technology solutions portfolio, a move which TD expects will enable it “to respond quickly to changing customer expectations by rolling out new features, updates, or entirely new financial products at an accelerated pace”.
This marks an expansion of the already established relationship between TD Bank and Google Cloud after the group previously adopted the vendor’s Google Kubernetes Engine (GKE) for TD Securities Automated Trading (TDSAT), the Chicago-based subsidiary of its investment banking unit, TD Securities.
TDSAT uses GKE for process automation and quantitative modelling across fixed income markets, resulting in the development of a “data-driven research platform” capable of processing large research workloads in trading.
Dan Bosman, SVP and CIO of TD Securities, claims the infrastructure has so far supported TDSAT with “compute-intensive quantitative analysis” while expanding the subsidiary’s “trading volumes and portfolio size”.
TD’s new partnership with Google Cloud will see the group attempt to replicate the same level of success across its entire portfolio.
Source: fintechfutures.com
The post TD Bank inks multi-year strategic partnership with Google Cloud appeared first on HIPTHER Alerts.
-
Latest News7 days ago
“The Hainan FTP and Me”: Looking at Hainan’s Transformations
-
Latest News5 days ago
Millions of people unite around doing good on the 18th International Good Deeds Day held yesterday worldwide
-
Latest News5 days ago
Banxso Acquires Australian ASIC License, Enhancing Its Global Trading Operations
-
Latest News3 days ago
BMO Announces Election of Board of Directors
-
Latest News5 days ago
135th Canton Fair Launches a Showcase of Innovative Products of New Collection to Lead Global Market Trends
-
Latest News4 days ago
HaloWallet Rebrands To Halo: Integrating SocialFi & AI To Revolutionize Social Influence Monetization
-
Latest News5 days ago
BII and FMO back BECIS with joint US$50 million financing facility supporting commercial and industrial renewables sector in South-East Asia
-
Latest News4 days ago
Former PayPal chief Dan Schulman joins Valor Capital as managing partner



